Cyber Threat Landscape of the Transport Sector in the EU
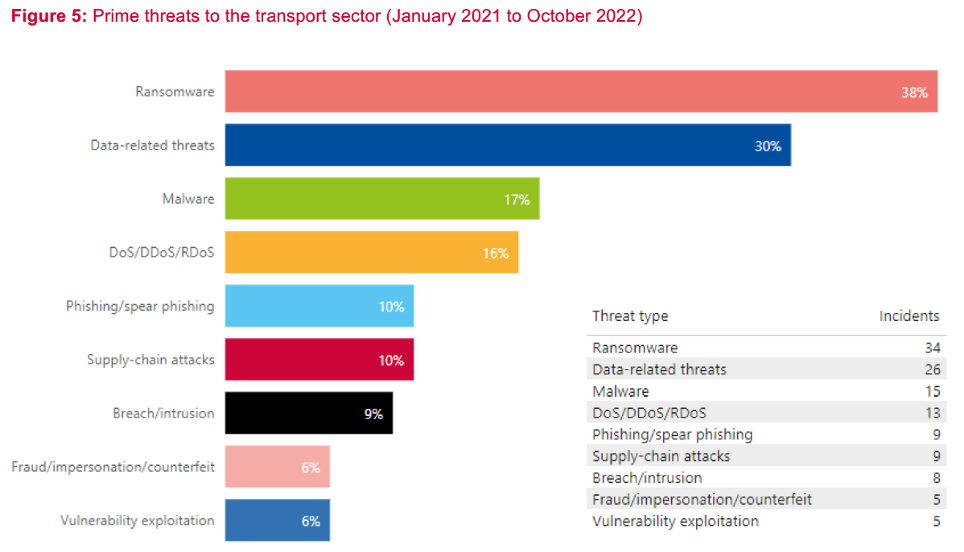
As the digital economy grows, digital crime grows with it. Soaring numbers of online and mobile interactions are creating millions of attack opportunities. The transport sector shows the same vulnerabilities to all other sectors and recent research has identified the following prime cyber threats for the sector:
- Ransomware attacks (38%),
- Data related threats (30%),
- Malware (17%),
- Denial-of-service (DoS), distributed denial-of-service (DDoS) and ransom denial-of-service (RDoS) attacks (16%),
- Phishing / spear phishing (10%),
- Supply-chain attacks (10%).
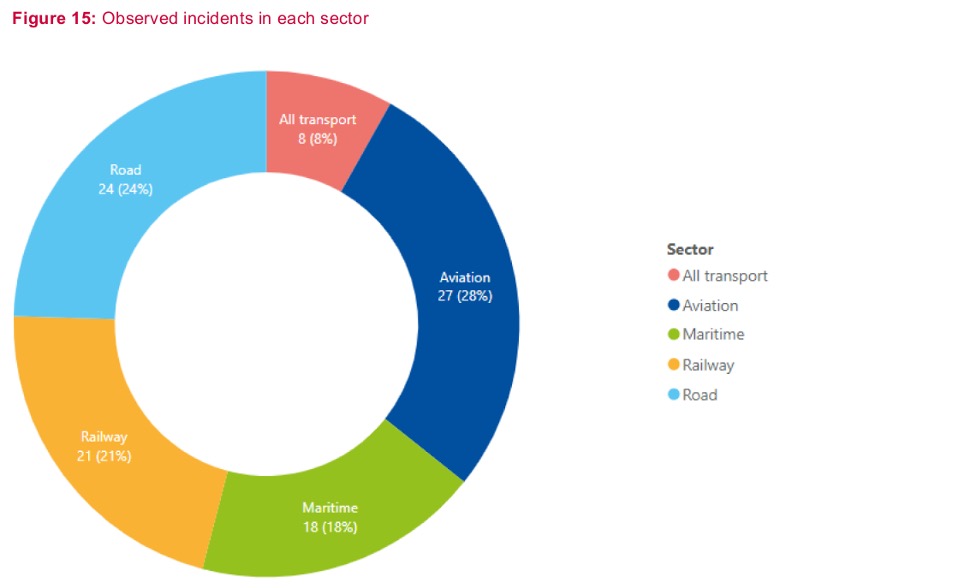
The aviation sector is facing multiple threats, with data-related threats being the most prominent, coupled by ransomware and malware. Customer data of airlines and proprietary information of original equipment manufacturers (OEM) are the prime targeted assets of the sector. In 2022, there has been a rise in the number of ransomware attacks affecting airports. Fraudulent websites impersonating airlines have become a significant threat in 2022.
The railway sector experiences ransomware and data-related threats primarily targeting IT systems like passenger services, ticketing systems, and mobile applications, causing service disruptions. Activist groups have been conducting DDoS attacks against railway companies with an increasing rate, primarily due to Russia's invasion of Ukraine.
The road transport sector faces predominantly ransomware attacks, followed by data-related threats and malware. Automotive industry, especially OEM and tier-X suppliers, has been targeted by ransomware leading to production disruptions. Data-related threats primarily target IT systems to acquire customer and employee data as well as proprietary information.
The maritime sector experiences ransomware, malware, and phishing attacks targeted towards port authorities, port operators, and manufacturers. State-sponsored attackers often carry out politically motivated attacks leading to operational disruptions at ports and vessels.
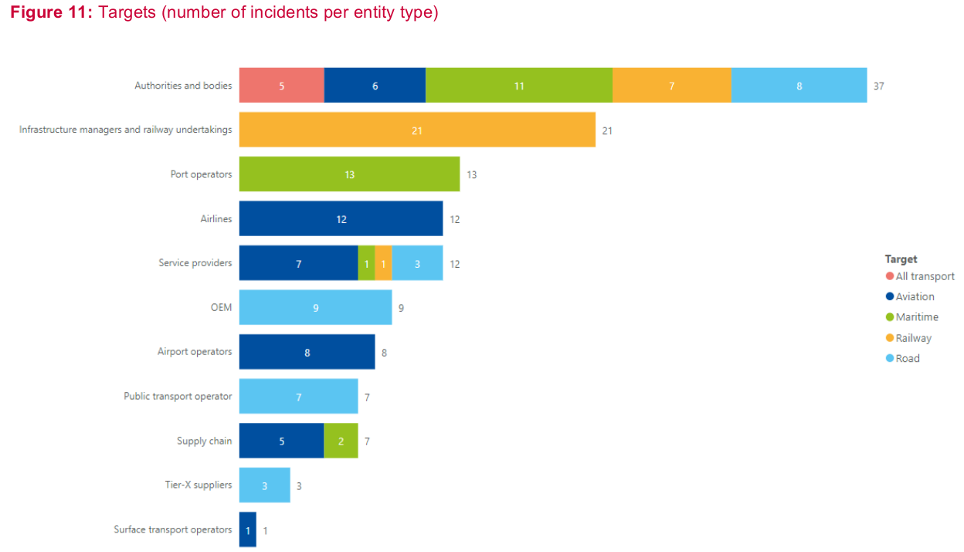
All transport modes had authorities and bodies that were being targeted, in fact 38% of the incidents targeted transport authorities. In the railway sector, incidents almost exclusively targeted railway undertakings and infrastructure managers. Similarly, port operators were the most affected entities in the maritime sector. These two sectors had only a few incidents targeting supply chain or service providers. This was not the case in the road sector, where OEM, tier-X suppliers and service providers were targeted, along with public transport operators. In the aviation sector, airlines and airport operators are the main targets, followed by service providers, surface transport operators and the supply chain.
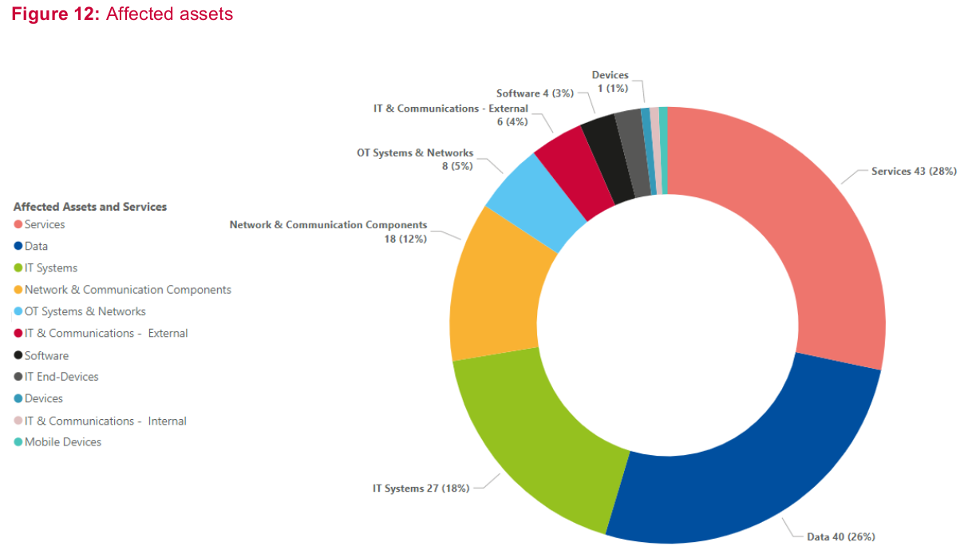
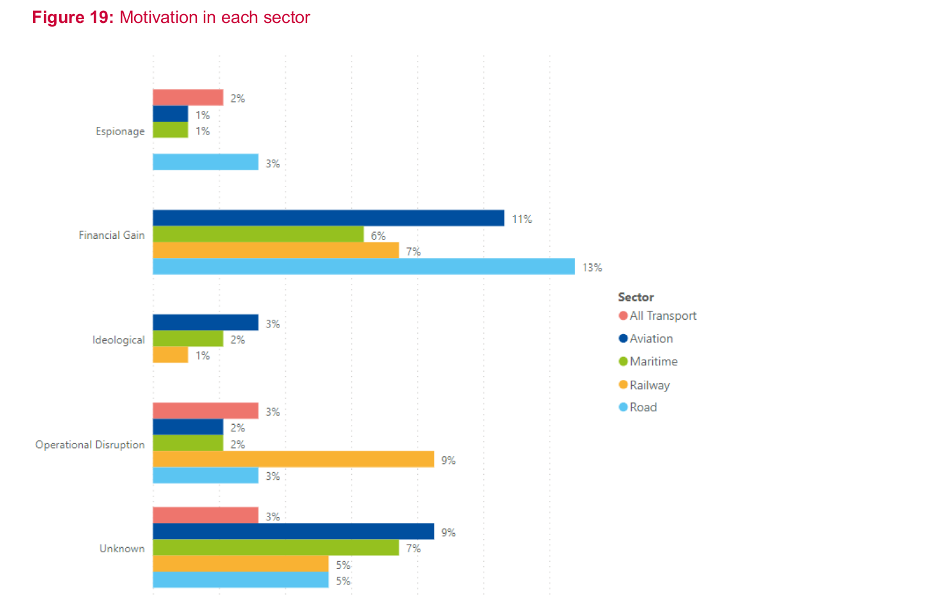
This and much more emerges from the recent Report issued by ENISA European Union Agency for Cybersecurity) on the cyber threat landscape of the transport sector in the period 2021-2022, accessible here: ENISA Transport Threat Landscape — ENISA (europa.eu)
A Secure Audit Manager for E-CORRIDOR: Graylog
The E-CORRIDOR framework foresees a component for auditing purposes that is part of the CSI (Common Security Infrastructure) subsystem. This component is called Secure Audit Manager and in our case it is implemented using Graylog Open Source tool.
As stated in Deliverable D5.2 “the Secure Audit Manager provides a service for tracing events that occur during the E-CORRIDOR framework operational activity; services such as creating audit trails of the DSA policies evaluations and of user access to E-CORRIDOR services”.
In order to receive log events, the GrayLog Log Management tool is required to configure Inputs for different types of sources. These components accept multiple message formats and communication mechanisms, and can further be integrated with configurable extractors to work on selected messages or even message subfields. The flexibility of Graylog has enabled the selection and tuning of messages flows suitable for different requirements by E-CORRIDOR applications and frameworks.
To facilitate E-CORRIDOR development partners, Graylog has been configured for receiving messages for the following four scenarios:
- Docker containers log information (all E-CORRIDOR subsystems run inside containers)
- System events happening inside VMs hosting ECORRIDOR platforms
- Messages from Application & ECORRIDOR platforms sent via REST API
- Java application messages through commonly opensource Log4j library
A Content Pack specific for E-CORRIDOR has been released to developers preconfiguring the following Graylog Inputs:
- Syslog for system events;
- GELF TCP for Docker container logs and Log4j appender;
- GELF HTTP for the REST API.
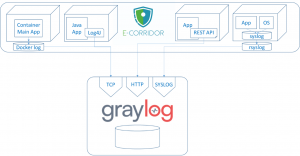
The following picture shows the interconnections between E-CORRIDOR components (applications & platform) with Graylog, highlighting the different channels used from the containers to the Inputs connectors.
As part of the typical internal dissemination activities, Graylog features and E-CORRIDOR specific integration have been presented to the partners together with a live Demo.
During this webinar the four different scenarios were analyzed in depth starting from the source code in the GitLab repository following with docker-compose configuration, also providing sample configuration for Log4j .
Live demo messages arriving from the four different scenarios have been collected by Graylog where they have been filtered by severity generating alarms and notifications to the operators.


