New and binding regulations of the United Nations, such as UNECE 155, show the importance of cybersecurity in increasingly connected, automated mobility.
Networks and attacks in vehicles get increasingly more complex and difficult to secure by hand. But as of now machine learning (ML) based approaches are not universally used in safety-critical systems, as the lack of insight into the results effectively prevents corrective actions.
We are developing a hybrid, lightweight anomaly detection system with a workflow whose results are traceable enough rule sets to understand as a human operator and reliably initiate mitigation measures.
Goals
- The development of trustworthy and explainable analysis methods for vehicle networks
- Detection and prevention in a unified structure for road and rail
- A ML-based security monitor that can detect anomalies and relations in data that are not captured in manually created rules
- Generation of rule sets that humans can read, comprehend and verify, as well as use as a base for the execution of mitigation actions
Key Contributions
- Notification of safety-relevant events
- Rule-based analysis services
- Transparency and explainability
- Lightweight classification
- Controls mitigation procedures
- Privacy and anonymization
- Conformity to the Ethics Guidelines
Approach
Initially data is collected from different sources, such as car sharing providers or vehicle manufacturers. Data is then anonymized, saved in a data lake and made available depending on access agreements through a system such as the E-Corridor ISI.
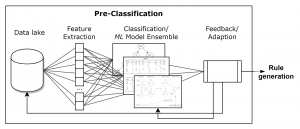
An ensemble of pre-classification approaches is then used to analyze the data for potential anomalies.
- Such a classification approach is already integrated into the E-Corridor IAI as the Automotive IDS service
- The pre-classification approaches often require high computational performance to detect anomalies and are therefore most suited to be run on a cloud system.
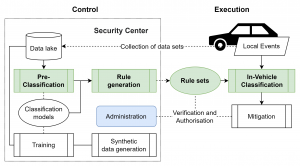
Using the pre-classification results, rule generation is used to generate rules.
- These sets based on simple logical and conditional operations on configurable values within a message and thus verifiable and comprehensible
- Generated rules are lightweight and run efficiently on low performance edge components
Manually generated rules can also be used as an input for rule generation, closing the gap between hand-crafted rule-based systems and MLS systems. The generated rules are then saved to the data lake and can be verified and transferred to the edge components within vehicles.
Results
- The proposed approach was chosen as a finalist at the 9th German IT Security Award
- Lightweight Anomaly Detection for Edge Computing
- Usable for implementation of regulations such as UNECE 155
- AUTOSAR-compliant integrable into connected vehicles
- Compliance with the European Commission’s Ethics guidelines for trustworthy AI


