A Shared Space for Cybersecurity Awareness in the Multimodal Transportation Domain
The Information Sharing and Analysis Center (ISAC) Pilot: A Shared Space for Cybersecurity Awareness in the Multimodal Transportation Domain
In today's interconnected world, where digital systems play a critical role in various industries, cybersecurity has become a paramount concern. The transportation sector is not immune to cyber attacks and possesses specific vulnerabilities that require particular protection. Transportation systems are facing a growing interest from attackers who are targeting vehicles and infrastructure. These attacks can lead to vehicle theft, service disruptions, and physical damage, posing a risk of terrorism and endangering lives.
To address these challenges and enhance the security posture of the transportation industry, E-Corridor introduces the Information Sharing and Analysis Center (ISAC) pilot, an infrastructure for analyzing and sharing cybersecurity data. It serves as a central hub for communication and raising awareness about cyber threats within the transportation domain.
By collecting comprehensive and up-to-date information on cyber threats, vulnerabilities, and incidents, the ISAC pilot aims to strengthen the industry's ability to detect, prevent, and respond to cyber attacks effectively.
The goals of the ISAC Pilot are the following:
- Collecting information: gathering cybersecurity-related data from both private and public entities
- Security analytics platform: a platform that enables the sharing of security data among different prosumers
- Information dispatch: disseminating relevant cybersecurity information and insights to all sectors of the transportation industry increasing awareness and enabling proactive measures against cyber threats.
- Cybersecurity analytics services: providing advanced analytics services in order to assist in identifying vulnerabilities, detecting threats, and offering tailored solutions to enhance their cybersecurity posture
Figure 1. Screenshot of the ISAC Portal homepage
The ISAC Pilot, in practice, offers a hybrid infrastructure that enables both edge-based and cloud-based operations for transportation service operators, supporting multimodal journeys similar to other pilots in the project. The primary focus of the ISAC pilot is to gather cybersecurity data from both public sources and private stakeholders within the transportation sectors. This data is securely uploaded to the ISAC portal, following established data sharing policies and utilizing the advanced capabilities of the E-CORRIDOR component.
Overall, the ISAC pilot offers valuable support to the transportation industry by providing a centralized platform for data collection, secure information sharing, advanced analytics, and sector-specific cybersecurity measures. By leveraging these capabilities, stakeholders can strengthen their defenses, stay informed about emerging threats, and proactively safeguard critical transportation systems and infrastructure.
Collaborative Approaches for Cyber Security in Cyber-Physical Systems
E-CORRIDOR is pleased to announce the publication of the following book edited by Theo Dimitrakos, Javier Lopez, Fabio Martinelli, and with contributions from several projects including E-CORRIDOR
Security and seamless authentication services in air-rail multimodal travels
Challenges and solutions for security and seamless authentication services in air-rail multimodal travels
Nowadays passenger’s travels are often multimodal. For example, a passenger may start its travel from home by using a car sharing service to reach the local train station and from this the nearest airport. And there may be multi-leg trips (i.e., stopping at intermediary places before reaching the final destination) and the passenger may use further modes of transfer.
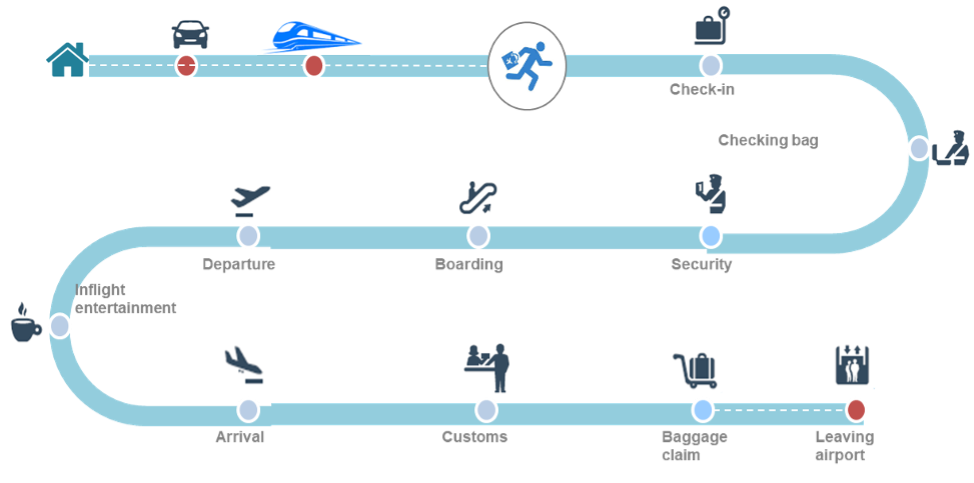
In the depicted scenario, multiple stakeholders and domains are involved, such as:
- passengers (including PRM, people with reduced mobility requiring assistance)
- airlines and railway companies
- airport and train stations
- ground operators
- shops and dining
Requirements and challenges
To deliver their services, information (including personal and sensitive data) is:
- collected
- verified
- (re-)shared
by Transportation Service Providers (TSPs).
The above-mentioned data processing operations can be limited, among the others by processes in place, limits pertaining the technological infrastructure, or lack of control over the shared information. All in all, this limits the capabilities provided by the services offered to the passengers (with impact to the passenger experience) or made available for the improving the TSPs operations.
Some of the challenges are related to the:
- Need for re-authentication among multiple stakeholders
- Manual operations for identification and authentication including incorrect entries
- Siloed knowledge in connected domains among carriers, operators, and service providers
- Discontinuous access to ground services, tedious connection and waiting time
The E-CORRIDOR approach and the Airport-Train Pilot solutions
In E-CORRIDOR the Airport and Train Pilot aims at tacking these challenges by exploiting the features of the E-CORRIDOR framework and the services designed for it. The use cases identified in the Pilot span from seamless passenger experience to identity management and improved airport operations.
“E-CORRIDOR offers distributed, edge-enabled and privacy-aware data analytics services thanks to its secure, collaborative and confidential framework for information sharing and analysis.”
Solutions designed for the Pilot cover:
- Seamless, robust, and privacy-aware authentication:
- Multi-factor authentication based on biometrics
- eIDAS connection for a pan-European identity management of the passenger’s data
- Situational awareness and passenger flow management:
- Privacy-aware analysis of camera feeds for security, efficiency, and crowd management
- Localization and wayfinding services for passengers (as well as PRM and assistants)
- Bring Your Own Device – based digital meet and greet services (to improve the passenger experience)
- Through the mobile enrollment at home
- Digital-kiosk for privacy-preserving preference matching
- Smart, intermodal, and secure airports (through data sharing with edge-hybrid computation)
- Connection with multi-modal Information Sharing and Analysis Center (ISAC) for cross-sector exchange of threats and vulnerabilities
- Controlled data sharing in a privacy-preserving manner
E-CORRIDOR Exploitation Workshop @ IMC22
E-CORRIDOR Exploitation Workshop @ IMC22
Consortium members from the E-CORRIDOR project gathered at the International Mobility Conference on October 25th & 26th in the picturesque seaside town of Sitges, Spain. Members actively contributed to two days of intense discussion around all aspects of the project, chaired by Dr. Fabio Martinelli, (CNR) and hosted graciously by local members FATCUAL and AMTU.
IMC 22
The conference, organised by the Association of Municipalities for Mobility and Urban Transport (AMTU), the Autoritat del Transport Metropolità de l’àrea de Barcelona (ATM), the Generalitat de Catalunya, the Diputació de Barcelona, the Catalan Association of Municipalities and Counties (ACM), and the Ajuntament de Sitges, aimed to promote various mobility sectors and upcoming changes to aid in the integration of technology into this sector.
The event was chosen as it offered members the opportunity to attend related presentations and network with individuals and companies in the same sectoral space. Key to the two-day gathering was an exploitation workshop and brainstorming session, chaired by Dr. Pat Lynch, (SETU) which allowed consortium members mutually explore commercial opportunities to exploit the technology and to provide a basis for the exploitation deliverable on the project’s completion.
Conference Outcome
Due to Covid restrictions this was the first opportunity for consortium members to meet in person. As a result, it was a key event, allowing all the opportunity to express their ideas and voice concerns about the platform before its full deployment. Good progress was made and many actions were taken from the conference. Follow up work will continue in the months to come.
Fully Homomorphic Encryption and its application to use-cases in a transport context
Fully homomorphic Encryption
Fully Homomorphic Encryption (FHE) is a recent cryptographic technology that allows a remote server to compute sensitive data in a privacy-preserving way. For example it can allow a hospital to perform statistics on encrypted input data from patients without knowing it in plain text, with medical confidentiality preserved. The applications of FHE can meet various domains, including multimodal transport.
What is fully homomorphic encryption ?
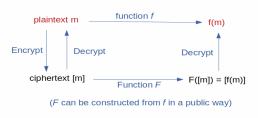
- Homomorphic encryption : encryption technique that allows for the performance of some computations directly on encrypted data, without knowing it in plain text ;
- Fully homomorphic encryption : homomorphic encryption that allows for the performance of (in theory) any kind of such computations.
- Recent area of research, only theoretical just a few years ago;
- The increase of the performances of homomorphic encryption is gradually breaking the technological barriers, allowing to scale up and use FHE in real life
- Basic workflow :
- A user encrypts its data and sends it to a remote server with a big storage capacity (potentially in a dynamic way) ;
- The user requests a computation on this input data to the server ;
- The server computes and sends the encrypted result to the user ;
- The user decrypts and gets the result in plain text;
- The server knows neither the input data nor the results of its own computations in plain text.
Some use-cases from a transport context
-
- Use-cases for blind searches in a database :
- Blind search of a driving license number in a blacklist, to check (in a privacy-preserving way) if a user that pretends to share a car has not been blacklisted before.
- Blind search of an IP address in a blacklist, to check (in a privacy-preserving way) that a connexion to a multimodal transport network is not from an IP address that has been blacklisted before
(network intrusion detection is important in transport context, as in many areas); - In an analogue way, FHE can allow a user to perform a blind search of an e-mail address or any other kind of data in a blacklist
(a server that performs homomorphic computations on encrypted data is agnostic in the kind of the data in clear).
- Use-case for blind set intersection :
- Blind computation of an intersection between the interests of a passenger and services provided by a transport company. For instance, a user can search which kinds of restaurants are provided in an airport among the kinds she likes, in a privacy-preserving way.
- Use-cases for blind searches in a database :
Real-life aspects and performances
- Our cluster dedicated to homomorphic encryption technologies uses 10 virtual machines hosted in OVH Cloud ;
- Performance (focus on the use-case of blind search of an IP address in a blacklist as an example) :
- 10 000 IP addresses checked in 5-6 seconds.
International Workshop on Privacy and Security of Multi-Modal Transport Systems (IWPSMTS 2022)
The IWPSMTS 2022 workshop was initially supported by: European Union’s Horizon 2020 E-Corridor project #883135
This workshop aimed to provide a forum for researchers and engineers in academia and industry to foster an exchange of research results, experiences, and products in the domain of security and privacy for multi-modal transport systems. Presentations focused on the advancement on the state of art in these fields and the adoption of developed technologies in several scenarios involving pilots from the domain.
The Symposium was held in conjunction with ARES 2022 and offered opportunities to become acquainted with recent results of research projects, meet potential project partners, and exchange ideas within the scientific community.
Presenters from E-Corridor at the conferece:
Roland Rieke (Fraunhofer SIT | ATHENE, Germany)
Stefano Sebastio (Collins ART, Ireland)
Florian Fenzl (Fraunhofer SIT | ATHENE, Germany)
Piotr Sobonski (Collins ART, Ireland)
Jean-Paul Bultel (CEA, France)
Henry Gadacz (Fraunhofer SIT | ATHENE, Germany)
Christian Plappert (Fraunhofer SIT | ATHENE, Germany)
Antoine Choffrut (CEA, France)
Hoang-Gia NGUYEN (CEA, France)
Marco de Vincenzi (CNR, Italy)
Implementation of an infrastructure for the ASI (advanced security infrastructure)
E-corridor Partner (CEA) has implemented an infrastructure for the ASI, and a component that provides fully homomorphic encryption (FHE) schemes running in this infrastructure.
The ASI (advanced security infrastructure) is the component that provides advanced cryptographic algorithms needed to the security of the whole E-CORRIDOR framework. Several sub-components are planned to run on this infrastructure, the FHE provider being one of them.
Fully homomorphic encryption (FHE) is a recent cryptographic technique that allows to encrypt (and decrypt) data in a way such that a remote server can compute on this encrypted data and output an encrypted result without knowing neither the data no this result in clear.
E-Corridor Updates
- UPEC have submitted a conference paper for IEEE CASE titled "Hybrid approach for anticipating human activities in Ambient Intelligence environments".
They are planning to submit another conference paper on the AT pilot to ACM Applied Computing (SAC) by September 2022. - CEA is defining the role of a server that provides a solution to compute on encrypted data for industrial people.
- CEA has implemented an infrastructure for the ASI, and a component that provides fully homomorphic encryption (FHE) schemes running in this infrastructure.
- CEA has implemented two IAI components (driving license checker, and IP blacklister) that interact with the ASI to compute on homomorphically encrypted data.
- CEA has designed a protocol to address a pilot use-case with ABE. This protocol allows or not a transaction between a passenger and a transport company according to a policy based on passenger's attributes.
- CEA has made three submissions for talks at the workshop IWPS HTS of the ARES conference, aboute solutions to address use-cases with FHE and ABE in contexts related with transports.
- E-CORRIDOR is organizing the International Workshop on Privacy and Security of Multi-Modal Transport Systems (IWPSMTS 2022) that will be held on August 23 2022 in conjunction with the 17th International Conference on Availability, Reliability and Security https://www.ares-conference.eu/workshops-eu-symposium/iwpsmts-2022/. IWPSMTS’22 aims at disseminating and exchange ideas on all the security aspects involving multi-modal transport services.
















